-What’s in your wallet?-
 Users assume DeFi is more secure, private, and less centralized than traditional financial systems and centralized exchanges. This belief was evident in the billions of dollars poured into DeFi protocols in 2020/2021. But users moving into DeFi with the idea of improving their privacy and security may end up with less of both.
Users assume DeFi is more secure, private, and less centralized than traditional financial systems and centralized exchanges. This belief was evident in the billions of dollars poured into DeFi protocols in 2020/2021. But users moving into DeFi with the idea of improving their privacy and security may end up with less of both.
Unknown to many, Web3/DeFi protocols and applications suffer from the same privacy and security issues plaguing the Web2 world. For example, many trackers used on DeFi sites record Ethereum addresses, while some trivially link users’ addresses with scripts written by phishers. This process opens unsuspecting users up to hacks, exploits and phishing scams. This piece article looks at these security issues in detail, what causes them and proposes some potential solutions.
Identified Privacy and Security Issues in Web3
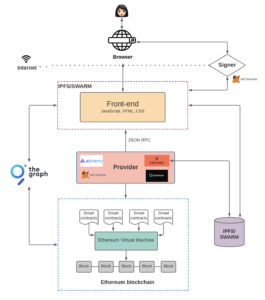
DeFi’s unique selling point is that it offers the same services traditional finance offers, like lending, borrowing, insurance, and exchanges, but with self-custody and decentralized features, all controlled by smart contracts. Additionally, protocol websites are designed differently from Web2 sites.
Image Source: Preethi Kasireddy
Instead of the conventional front end built to interact with the database back end, dApps contain a simple front end filled with trackers to interact with the blockchain-based back end, which uses wallet software running in each user’s browser. This unorthodox design and integration have worked so far. However, it raises some questions about privacy and security: How well do these dApps and protocols protect the user’s financial information? What vectors are available for attackers to exploit and steal funds? And what are the risks of using third-party trackers on DeFi websites?
As established above, third-party scripts open DeFi users to potential financial risks as bad actors can exploit them to reveal sensitive information. How? Numerous DeFi sites use services like Google Tag Manager and Google Analytics to collect users’ data. However, this data collation has been heavily criticized because they leak users’ financial activities and Ethereum addresses.
Recently, the EU declared that using Google Analytics violates the 2020 Schrems II judgement. Additionally, countries in the EU have warned against using Google Analytics because it may soon be illegal, while others advice brands to use other analytics alternatives. Most DeFi websites use at least one Google script/tool, which is convenient and insightful, but the amount of data they leak is sensitive.
For a clear example of the data leaks and risks involved, let’s look at 1inch. 1inch’s landing page is embedded with third-party scripts, one of which is Google Analytics. This particular script reveals users’ sensitive browsing activity because each 1inch url is encoded with what token the user is interested in, e.g., https://app.1inch.io/#/1/unified/swap/USDT/UNI. The above url shows that the user selected the USDT and UNI tokens to swap. Furthermore, 1inch puts each user’s Ethereum address in an “event label” on Google Analytics. In doing so, Google can link the user’s wallet address with the Personal Identifiable Information (PII) they likely have about the user.
What’s in Your Wallet?
DeFi users manage their funds in software wallets that function as browser extensions. These extension wallets store each user’s private key while providing a UI for using funds. As of September 2022, the most popular in-browser wallet is MetaMask. However, the risk is not inherent in MetaMask or whatever wallet the user prefers. Instead, the risk is in the protocol website – if it embeds scripts, those scripts can interact with the wallet API, which facilitates phishing attacks.
For example, 1inch has a chat button for contacting the support staff. The widget contains JavaScript, which has control over 1inch’s DOM. This framework is not surprising, as many websites use the script. However, in this case, once a user connects their MetaMask wallet to 1inch, both 1inch and the chat widget can interact with the Ethereum provider API integrated with MetaMask. Furthermore, anyone accessing the chat widget’s infrastructure can phish out the user or directly make a transaction with the wallet. Of course, the transaction must be approved by the user, but if it is well-timed, it could fool some unsuspecting users.
Potential Solution
Integrating scripts to DeFi websites always brings potential risks, considering the amount of money involved. That said, the problem is not without solutions. One such solution is the implementation of a privacy-enhancing patch for the MetaMask wallet extension to prevent possible scams and exploits. This patch replaces the user’s actual Ethereum address with derived, site-specific addresses, making it harder for DeFi sites and trackers to track the user’s activity across sites. The purpose of the fake address is to dissociate it from the user’s identity and digital footprint. In addition, when making a transaction, the website should intercept the transactions to replace the phoney wallet address with the real version. Doing this will validate the RPC calls of the wallet. Finally, DeFi developers should use self-hosted analytics and consider privacy and threat models when creating protocols.
Conclusion
DeFi offers various important financial services. However, the industry faces its fair share of risks and security difficulties because of the possibilities. For example, 2022 has seen losses above $3 billion – October has been the biggest month for hackers, with losses exceeding $700 million. Currently, there is no straightforward way to eliminate these hacks and exploits. That said, DeFi users should be aware of the security issues involved and mitigate risks.
About THRESH0LD
THRESH0LD offers a single, simple-to-integrate API that helps digital asset businesses such as crypto exchanges, payment processors and OTC solutions cut tx fees, save time and enhance security.
THRESH0LD supports 44 blockchain protocols and with our DeFiBridge, you can enable swaps across many thousands of assets.Found this piece interesting? Check out our other blog posts.