-A Review of their Impact-
Due to the increasing rate of flash loan attacks, there is an ongoing debate within the DeFi space regarding the practicality of flash loans. While flash loans are outstanding, certain malicious DeFi users have found ways to benefit from them by leveraging one or multiple DeFi protocols to manipulate the market. This has stirred a lot of controversy surrounding flash loans – because they provide loans without collateral, they are susceptible to exploitative attacks.
In this piece, we will look at flash loan attacks, understand their effects, and how to mitigate their effects possibly.
What are Flash loan Attacks in DeFi
Flash loan attacks are typically price manipulations on the blockchain. Flash loans are only valid in one blockchain transaction. If the borrower fails to repay the debt before the end of the transaction, it is reverted. Because of this condition, there are some attack vectors that are exploited by users.
For example, a user can take a massive loan (token T) from one protocol, then swap token Z for another token (Y) on a DEX, effectively tanking Token Z’s price. After that, they deposit the purchased token Ys as collateral on another DeFi protocol that only gets its prices from the previously used DEX allowing them to borrow more of token A. After this, a portion of the tokens is used to fully pay off the original flash loan while they get to keep the excess. This process is swift and repeated as often as they want, to increase their profits while leaving little to no trace.
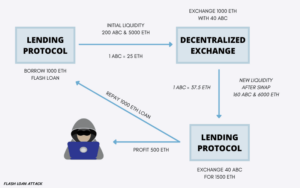
Image Source: The Crypto Times
Flash Loan Attack Types
- Oracle manipulations:
Oracle/price manipulations are the #1 cause/type of loan attacks in DeFi. Pricing information on decentralized exchanges like Uniswap, Sushi, and Curve solely depends on current liquidity. Because of this feature, any attacker can manipulate and crash the prices of the tokens on these DEXes with the loans they take out.
- Front Running
Because blockchain transactions are available online, attackers can identify potential loans for attacks and make a transaction with a higher gas fee before that loan transaction goes through. For example, a whale is about to dump a token they hold, so they pay extra gas to dump its tokens first, meaning they profit from the current prices.
- Reentrancy
Reentrancy attacks occur when the protocol’s smart contracts have a function that makes external calls to other untrusted contracts before resolving transactions. Once an attacker gains control of this smart contract, they can repeatedly make a recursive call to the original function, thereby repeating the transactions.
Their Effects on the DeFi Space
There have been ten historic flash loan attacks on Ethereum DeFi protocols, all amounting to a loss of $142,000,000. One of the most notorious exploits is the attack on the bZx protocol, where the attacker made away with $600,000 by borrowing funds and quickly swapping them for stablecoins (sUSD). The stablecoins were stored in a smart contract allowing the attacker to manipulate the price by placing a large buy order, which pushed the price of sUSD to $2, double its pegged value. The attacker then took a larger loan, repaid his previous loans, and took his profit.
Other notable attacks have occurred, but the bZx attacks enlightened the DeFi community about the apparent risks. One such risk researchers found is that the liquidity provider and lender are always paying for the prices of the attacks. In addition, other DeFi users, apart from the attacker, can also benefit from the price manipulation. This is because the attacker cannot arbitrage the artificially induced price difference during the loan transaction.
How to Mitigate Flash Loan Attacks
Certain strategies exist to prevent – but not fully eliminate – flash loan-enabled attacks. Despite that limitation, anyone can reuse these strategies to prevent flash loans from occurring in the first place. Some examples include:
- Using strong oracles
For context, decentralized exchanges can not communicate price information with one another. Hence token prices are always different. Many flash loan attackers have relied on this limitation to distort market prices for profit. This type of attack can be prevented when users rely on the aggregated prices of a token on different exchanges instead of a single or few exchanges. For example: using Chainlink’s oracle feed while checking different DEXes. Doing this would reduce the risk of making transactions with incorrect price information. However, the user runs the risk of transacting with increased gas fees.
- Keeping slippage to a certain limit
Slippage is when a token’s price fluctuates between the time of the transaction and the time it is confirmed and added to a block. Often, slippage occurs naturally; however, it can be induced on purpose to allow the attacker to profit from the transaction. Decentralized exchanges can limit slippage percentages to a certain amount, for example, 2 – 3%. This method effectively restricts the fluctuation margin, but attackers can still cause slippage up to the maximum percentage. At best, the method keeps the damage minimal. Additionally, if set incorrectly, slippage limits may be too restrictive or loose.
Bottom Line
Flash loans are a great addition to DeFi’s ecosystem. They are currently prone to attack, but the attacks may reduce in the future. The attacks are common because they are affordable, require little capital, and with low risk. The space needs more protocols that deploy secure smart contracts and decentralized oracles for optimal pricing. When this goal is achieved, loan attacks will decrease and hopefully vanish from the horizon.
About THRESH0LD
THRESH0LD offers a single, simple-to-integrate API that helps digital asset businesses such as crypto exchanges, payment processors and OTC solutions cut tx fees, save time and enhance security.
THRESH0LD supports 44 blockchain protocols and with our DeFiBridge, you can enable swaps across many thousands of assets.
Found this piece interesting? Check out our other blog posts.





